Imagine the heart-stopping moment: You wake up, grab your phone, and your entire social media world has been flipped upside down. Your photos gone, your contacts bombarded with strange messages, reputation at stake, and maybe even your finances threatened. In 2025, this nightmare is a reality for millions. Social media is not just about connecting with friends anymore, it’s where we work, socialize, market, shop, and even manage our identities. But this stage is now crawling with sophisticated attackers, making every post, friend request, and clicking a potential entry point for chaos.
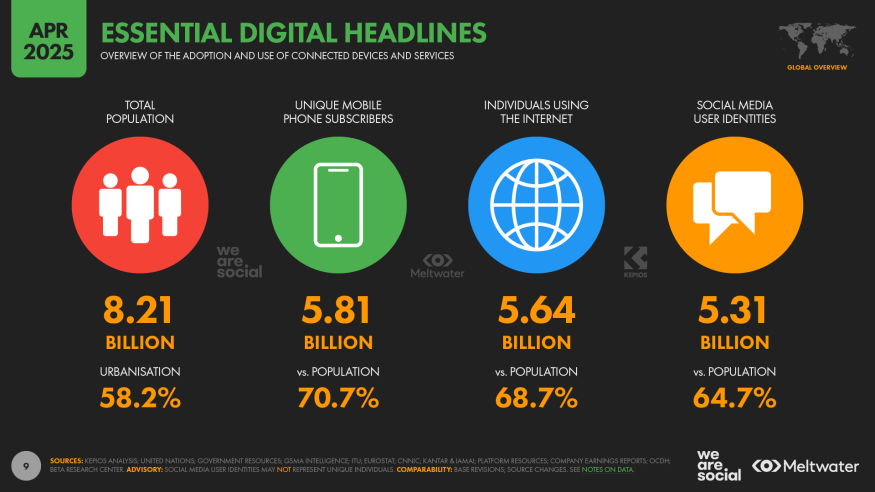
The numbers are staggering and the enemy is evolving. As we hit over 5.31 billion social media users around the world at the start of April 2025, equating to 64.7% of the total global population. Every single click and like becomes data in a vast digital ocean, irresistible to hackers. It’s never been more crucial to turn your awareness into action. If you think your account is safe because you’re careful, this article will awaken you to new realities with real statistics, sharp analysis, and foolproof strategies.
Your Digital Life is Under Attack: Are You Ready to Fight Back?
How Did We Get Here?
Social media began as a digital playground. MySpace, Facebook, and early Twitter unleashed a wave of sharing, self-expression, and global connection. At that time, security was a simple password, and you were in. Gradually, our online personas started carrying value, becoming an extension of ourselves. Platforms drew in brands, governments, celebrities, journalists, and criminals. What started as photo sharing evolved into multi-billion-dollar ecosystems for influence, commerce, and identity.
But for every evolution, new threats took over. When social media became central to daily life, cybercrime shifted its sights. Phishing attempts, malware, impersonations, and scam links proliferated. The click of a button was all it took to set a chain reaction. As platforms interconnected, a compromise on one could domino across your digital life. By 2025, cyberattacks are relentless, account takeovers rose 78% since 2023, with recovery times averaging 17 days and billions in financial losses.
CyberDefense Analytics reports that social engineering efforts and search terms to hire a hacker for social media aimed at platform users have increased by 43% in just the past year.
“Technically, today’s platforms are more secure than they have ever been. The problem is that hackers are now emphasizing the human aspect, leveraging trust, manipulating emotions, and profiting from user behavior patterns that get past security policies.”
Mark Reynolds, former security architect at a major social media platform.
The battleground has changed. Sophisticated attackers blend psychological tricks with technical bluffs. They are targeting not just your data, but your identity, relationships, and opportunities.
The Evolution of Hacks
Let’s be clear: it’s not just “other people.” Even tech-savvy users and professionals fall victim. In a 2025 survey, 489 million Instagram Accounts Scraped and Listed for Sale on Dark Web. A marketing director recounts how a reused, “personalized” password led to ransomware demands, fake posts, and weeks of recovery even though they followed basic internet hygiene.
AI now creates convincing text, video, and audio deepfakes to trick friends and get sensitive data, and hackers use multi-platform tactics to lock out users and demand ransom. The average time to recover from an attack is 17 days. Some never get their accounts back at all.
Also Read: The 10 Most Notorious Hackers
This sophisticated evolution of attack vectors means that even seemingly simple interactions can have devastating consequences. Attackers leverage AI to craft hyper-realistic phishing attempts, where a voice clone of a loved one or a video of a CEO can trick victims into revealing credentials or making fraudulent transfers. These deepfake-powered scams are increasingly difficult to distinguish from genuine communications, bypassing traditional filters and exploiting human trust at an unprecedented scale.
Furthermore, the dark web has become a bustling marketplace for stolen data, where compromised accounts and personal information are traded for nefarious purposes, fueling subsequent, more targeted attacks. The multi-platform nature of modern cybercrime means that a single point of entry, like a weak social media password, can rapidly lead to a cascade of breaches across emails, banking, and other vital online services, making recovery a complex and arduous process.
How Social Media Platforms Are Fighting Back?
Platforms aren’t standing still. Major investments have made networks technically stronger than ever. Machine learning now flags billions of fake accounts and filters dangerous content in real time.
Yet attackers are adapting faster, especially exploiting users directly. 321 cyber threats were blocked every second, but social engineering, the art of tricking people, not computers, is at an all-time high, responsible for 86% of attempted attacks in late 2024. In response, platforms are:
- Mandating 2FA for certain users and accounts.
- Investing in deepfake and AI-generated content detection.
- Holding regular security audits and rolling out user security education campaigns.
- Shutting down obvious fake accounts and scam operations before they proliferate.
The True Scale of the Danger
Let’s look at why protecting your social media is non-negotiable today
- In 2025, 429 million accounts were compromised, a number forecasted to reach 580 million by year-end.
- The biggest ever data leak to date exposed 4 billion records, including WeChat data, bank details, and Alipay profile information of hundreds of millions of users, primarily from China.
There’s more: The compromised passwords are no longer a rare problem; it’s a widespread crisis affecting everyone from teens to CEOs.
Why Social Media Makes an Attractive Target?
It takes 20 years to build a reputation and a few minutes of a cyber-incident to ruin it.” Stéphane Nappo, Global Chief Information Security Officer (CISO), Groupe SEB
Criminals are motivated by one thing: value.
| Category | Examples | Why It’s Valuable to Attackers |
| Personal details | Full names, birth dates, email addresses, phone numbers, locations, photos | Used for identity theft, targeted phishing, impersonation, and credential stuffing; sells well on darknet markets |
| Professional connections | Access to business pages, brand accounts, professional contacts, colleagues | Enables larger-scale scams, business email compromise, reputational attacks, and brand fraud |
| Financial hooks | Connected payment info, ad accounts, invoice details, opportunities for scams | Allows ransom, unauthorized transactions, ad fraud, money laundering, and stealing business or personal funds |
| Trust networks | Friends, followers, family members, community groups, private DMs | Facilitates phishing, spreading malware, and expanding attacks via trusted accounts and social engineering |
In 2025, the game has changed. Technical defenses are strong, but attackers exploit the human element, our trust, curiosity, and the speed with which we click. Attackers have moved beyond simply guessing passwords to deploying multi-stage attacks i.e., phishing, social engineering, session hijacking, SIM swapping, and fake verification badge scams.
This is why even sophisticated users are caught off guard as hackers now mimic personal communication styles using AI, craft believable deepfake videos and audio, and overwhelm users with multi-factor authentication (MFA) fatigue until they make a mistake.
Why Most “Good Habits” Are No Longer Enough
It’s 2025, and old assumptions don’t cut it:
- Changing your password once a year? Too slow.
- Clicking only on links from people you “know”? Your friend’s account may have been hijacked.
- Relying on your platform’s built-in alerts? Hackers now even bypass those.
The biggest mistakes people make are:
- Reusing passwords across different platforms.
- Ignoring two-factor authentication (2FA).
- Over-sharing personal information.
- Failing to audit their account for suspicious device logins or connected apps.
- Neglecting privacy settings.
The consequences go beyond embarrassment. A breach can threaten your finances, relationships, or even career.
Seven Essential Shields to Protect Your Accounts Now
1. Build Unbreakable Passwords
Move beyond “password123” or your pet’s name. Today, a strong password means at least 14 characters, a random mix of letters, numbers, and symbols unrelated to anything easy to guess. Password managers are your best friend as they generate and store passwords and alert you if a breach is detected.
Tools to try: 1Password, LastPass, Bitwarden, Dashlane.
2. Double Your Locks with Two-Factor Authentication (2FA)
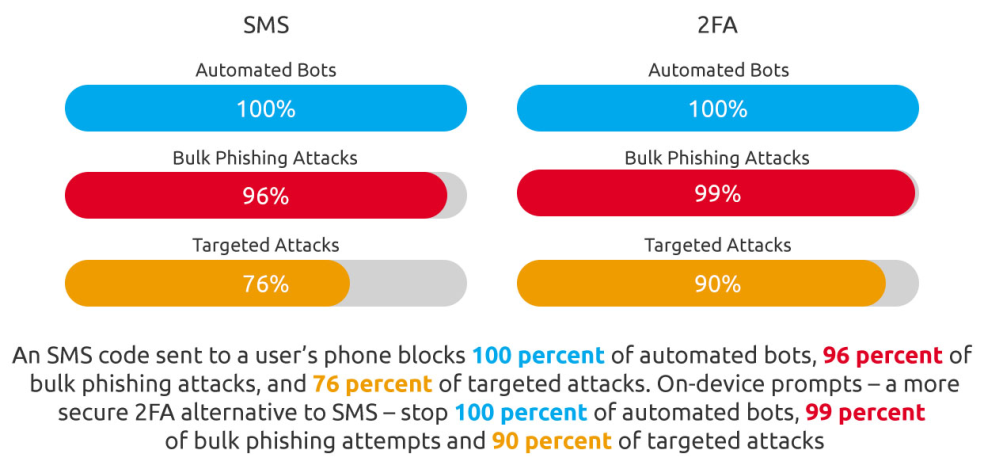
Passwords alone are no longer enough. 2FA adds another needed wall: a one-time code sent to your device, an authentication app, or even a physical key device. This can block over 76% of credential attacks. Most major platforms support 2FA today. Always prefer app-based authentication (like Google Authenticator or Authy) or a hardware key. SMS-based codes are better than nothing, but are vulnerable to SIM-swapping attacks.
3. Audit Your Digital Footprints
Most people still have old social media accounts or connected third-party apps they rarely use, and these neglected logins often become major security weak points. Conducting regular reviews of your account settings is essential: carefully check for suspicious logins or devices you do not recognize, and promptly remove any unused apps or third-party integrations that have lingering access. It’s equally important to actively search for and report imposter accounts trying to use your name or brand identity. Making this a monthly routine can reduce your risk of compromise. Unfortunately, many breaches happen simply because users ignore warnings or overlook unfamiliar logins in their account settings, leaving an easy path for attackers.
4. Secure Your Privacy Settings
Social platforms now offer detailed controls over who can see your posts, profile information, and activity but by default, many settings are wide open, making you more vulnerable than you might think. Tightening your privacy settings is more than just a precaution, it’s a necessity. Limit visibility of your posts, friend list, and contact details to only trusted people, and always approve friend or follower requests manually to keep out suspicious profiles.
Similarly, blocking spam accounts and impersonators is critical, as they are often used for social engineering and phishing schemes. Be cautious about sharing your location, tags, and photo albums, and avoid disclosing too many personal or professional milestones online.
5. Outsmart Phishers and Scammers
Social engineering attacks (psychological manipulation, fake links, scam messages) now account for over 43% more incidents year-over-year. Attackers adapt rapidly, pulling in emotion, urgency, or fear to trick you.
How to win?
- Never click on links from unknown or unexpected sources inside DMs.
- Be wary of password reset messages or pop-ups asking for verification.
- Watch for slight misspellings in usernames or web addresses.
- Ignore random requests for money, urgent actions, or “giveaways.”
- Verify the source using phone or alternate communication.
Training yourself and those around you is the best defense.
6. Guard Your Mobile Devices and Home Network
Your phone is often the “key” to your social lives. If compromised, attackers can seize your social accounts via text codes and apps.
- Keep devices updated with the latest security patches.
- Use device locks (PIN, face/fingerprint recognition).
- Avoid logging into social accounts on public or shared computers.
- Never use public Wi-Fi for logging in unless you use a VPN.
- Regularly back up important content off-platform.
Real-time concern: A 2024 report found that 90% of successful cyberattacks begin from endpoint devices like phones or laptops. And apps downloaded from outside official app stores are 200% more likely to contain malware.
7. Respond Fast to Incidents
If you spot something suspicious on your social media like unfamiliar logins, unauthorized posts, or password change alerts, immediate action is critical. Change your passwords on “all affected platforms” without delay, as attackers often move quickly to exploit linked accounts. Make sure to enable or reset two-factor authentication (2FA), adding a strong layer of protection that can prevent further unauthorized access.
Let your contacts know what happened so they don’t fall for fraudulent messages from your compromised account, a tactic now used in most of the social media attacks in 2025. Go through your account’s active sessions and connected devices list; log out anything you do not recognize to block intruders. Use your platform’s help center or dedicated recovery channels to report the breach and speed up the recovery process.
For those responsible for business continuity within our organizations, we have to make sure that our plans take into account the likely time and priority order of the recovery. We might put the RTO of an activity at 24 hours, but after looking at the recovery priority, we find out that the applications which support our activity are lower down the priority list and not likely to be recovered until day 7. Once we understand this, we can go back to our strategy for the activity, and work out how to continue the activity at a minimum level for 7 days. So, the more we understand about the recovery after a cyber incident, the better our planning will be, and we can challenge our recovery assumptions and see if our RTOs for applications and activities are realistic. 15% of cyber teams spend more than seven (7) hours a week managing false positives.

Humans Are the Best Firewalls
No matter how sophisticated social media security systems become, the ultimate defense always comes down to the user. Hackers are persistent in finding ways to sidestep technical solutions by manipulating human emotions, urgency, and predictable habits. Remaining skeptical, even of messages that appear convincing or come from known contacts, is essential. As social media phishing scams in 2025 are now disguised as personal or urgent requests.
| Statistic | Value |
| Phishing emails sent daily | 3.4 billion |
| Percentage of global email traffic that is phishing | 1.2% |
| Percentage of all breaches involving phishing (2022–2024) | 36% |
| Percentage of malware infections originating from phishing | 94% |
| Average cost of a phishing breach (YoY increase) | $4.88 million (up 9.7% YoY) |
Educating your friends and family is just as important, since a single compromised user can open doors for wider attacks. Studies show that when people actively share security tips with their circles, overall incident rates drop. Continually updating your security skills is crucial because platforms frequently change their settings and features, often in response to new threats. Advocating for transparent default settings and improved user protections is more important than ever, given that most users believe platforms don’t do enough to protect their privacy.
Finally, staying informed about the latest threats and updates ensures you’re ready for whatever comes next; with the threat landscape evolving every month, treating security as an ongoing practice not a one-time checklist is the smartest strategy in 2025.
Expert Analysis:
“Technically, today’s platforms are more secure than they have ever been. The problem is that hackers are now emphasizing the human aspect, leveraging trust, manipulating emotions, and profiting from user behavior patterns that get past security policies.”
Mark Reynolds, Former Security Architect at a Major Social Media Platform:
This quote precisely captures the core challenge. While platforms invest heavily in technology, the weakest link remains the user. Attackers have become adept at social engineering, understanding that human psychology is often easier to breach than robust technical defenses. This validates the article’s focus on user education and awareness as crucial components of defense.
“If you think tech will solve your security problems, you don’t understand either.” (Often quoted as: “If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.”). Bruce Schneier, Renowned Cryptographer and Security Technologist:
Schneier’s long-standing insight is more relevant than ever in 2025. This underscores that technological solutions alone are insufficient; a holistic approach that includes user behavior and organizational processes is paramount. The article’s emphasis on “foolproof strategies” like building unbreakable passwords and using 2FA, while seemingly technical, ultimately relies on consistent human action.
Also Read: Top 12 Cybersecurity Tips Everyone Should Know in 2025
The Future of Social Media Security
Looking ahead into 2025 and beyond, social media’s transformation is just beginning, with continual growth accelerated by deeper AI integration, constantly evolving applications, and an ever-increasing portion of our lives shifting online. This surge means numbers are rising relentlessly both in new users and in attempted breaches. Several key trends are shaping the future: decentralized platforms may address privacy concerns but also create new challenges for unified security management; biometric and hardware-based authentication methods, like fingerprints, facial recognition, and physical security keys, are poised to phase out traditional passwords, making logins both easier and more secure.
Automated security agents powered by advanced AI are emerging to monitor accounts in real time and alert users before hackers can gain a foothold. At the same time, growing legislation and regulatory pressure will force social platforms to improve user protections, though attackers will inevitably look for new loopholes. The good news is actionable: using unique passwords for every account, activating strong two-factor authentication, and conducting regular account audits can cut your risk of being hacked by over 90%. Individuals and organizations that treat digital security as a daily routine just like brushing their teeth will have a significant advantage in this rapidly shifting landscape
The challenge is only growing, but so are the solutions. Will you be ready?
Frequently Asked Questions
1. What should I do first if my social media is hacked?
Start by changing your password on every affected site, enable or reset two-factor authentication, remove unknown devices from your account settings, and notify friends not to trust any messages from your hacked account. Use your platform’s official help center for guidance.
2. How common is social media hacking in 2025?
Highly common 1 in 5 users face hacking attempts annually, and over 429 million accounts were compromised so far this year.
3. Why is two-factor authentication so important?
Because 2FA blocks over 76% of credential attacks, even if your password is stolen. App-based verification is safer than SMS codes.
4. Where do I check if my data has been exposed in a breach?
Use official tools like Have I Been Pwned or check your password manager’s warning system for breaches tied to your email or usernames.
5. How to stay safe online?
To stay safe online, it’s crucial to prioritize strong passwords, enable two-factor authentication, be cautious of suspicious links and requests, keep your software updated, and be mindful of what you share online. Additionally, consider using a VPN, especially on public Wi-Fi, and regularly backing up your data.
6. What is social media security?
Social media security involves a set of policies and procedures used to safeguard user information, privacy and accounts on various social networking sites. It provides security against online harassment, unauthorized access, phishing attacks, malware, data breaches and identity theft.




