When the enemy is a moving target it’s often only possible to look at the past to try to predict the future. Such is the case in IT security where the attackers are constantly developing new ways of breaking in and achieving their nefarious goals.
Presented by: Background Check Guide
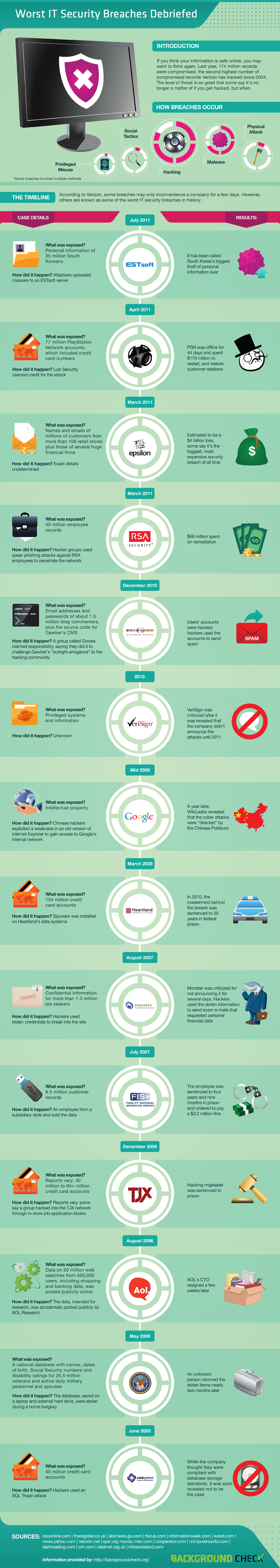
This graphic depicts some of the biggest security breaches in IT history, breaking down the what and how of the attacks as well as the end results. Click to enlarge.


Leave a Reply