Tag: Hacking
Powered by TechAbout403 Stories

New gadget remembers where you parked
It’s the age old problem. You park your car in the parking garage, but you can’t remember where. Was it...

Your data might already be breached
If you think hackers aren’t trying to infiltrate your business or organization, you are probably lying to yourself. The average...

Is your password secure?
We all know the old rule of never recycling passwords, but how many of us actually follow this advice? In...

5 lessons from recent data breaches
Technology has revolutionized the way we do everything, including shopping. Now instead of having to go to the store and...
![Preventing ATM Theft [Infographic]](https://www.techi.com/wp-content/uploads/2014/09/6134-close-up-of-three-credit-cards-or-a-264x176.jpg)
Preventing ATM Theft [Infographic]
Every year, ATM skimming costs America $8.5 billion, most of which is paid by consumers and institutions. Skimming accounts for...

Your data is at risk: 5 eays to protect it
Heartbleed made the rounds in the media as the security threat du jour. What made Heartbleed so dangerous was that...

First “Heartbleed Attack” makes wave
In the past couple of weeks you’ve probably received emails, Facebook posts, or tweets warning about the Heartbleed virus, but...

Your smartphone could be hacking your life
The smartphone is a tricky device and sometimes the lines between master and servant are blurred. On one hand we...
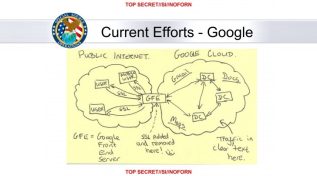
Why the NSA tapping of Google and Yahoo clouds is more dangerous than PRISM
Could we be getting "NSA fatigue"? No, I'm not talking about the obvious weariness that we have about the National...

New ways hackers are stealing your identity
As you read this, hackers everywhere are hard at work trying to obtain your personal information and steal your identity....

How to easily protect your digital identity
Protecting your digital identity doesn't take a degree in computer science. Follow these 5 easy steps to secure your personal...

Where is your POS system vulnerable?
When it comes to point-of-sale, there are a few vulnerabilities that you probably didn't even know were there. In 2012, the...

Tips to protect your social media accounts
Imagine the heart-stopping moment: You wake up, grab your phone, and your entire social media world has been flipped upside...

3 quick iPhone hacks that you probably didn’t know
The iPhone has been blazing trails in the smartphone industry for 5 years now. It's domination has been threatened lately...

How social engineering works
When you combine the common old school methods of grifting with the technological advancements of hacking and social research, you...

Convicted hacker allowed in prison IT class, hacks prison’s computer systems
There are plenty of stories about dumb criminals doing dumb things, but we don't get to hear as often about...
A basic guide to getting hacked
Nobody wants to get hacked. The very concept is terrifying to many and at the least a personal violation to...
@BurgerKing learns the hard way that your password must be secure
It may never stop happening. Twitter accounts are hacked every hour of every day. Every now and then, a big...

If you still hate Apple Maps, here are 5 alternatives
Apple has been the butt end of many jokes since it launched its failure of an app: Apple Maps. Since...

Duh. The easiest way to stop hackers is with real passwords.
One of the most personal online violations that can occur to anyone is getting hacked. It could be a personal...